Security Breach Recovery Services
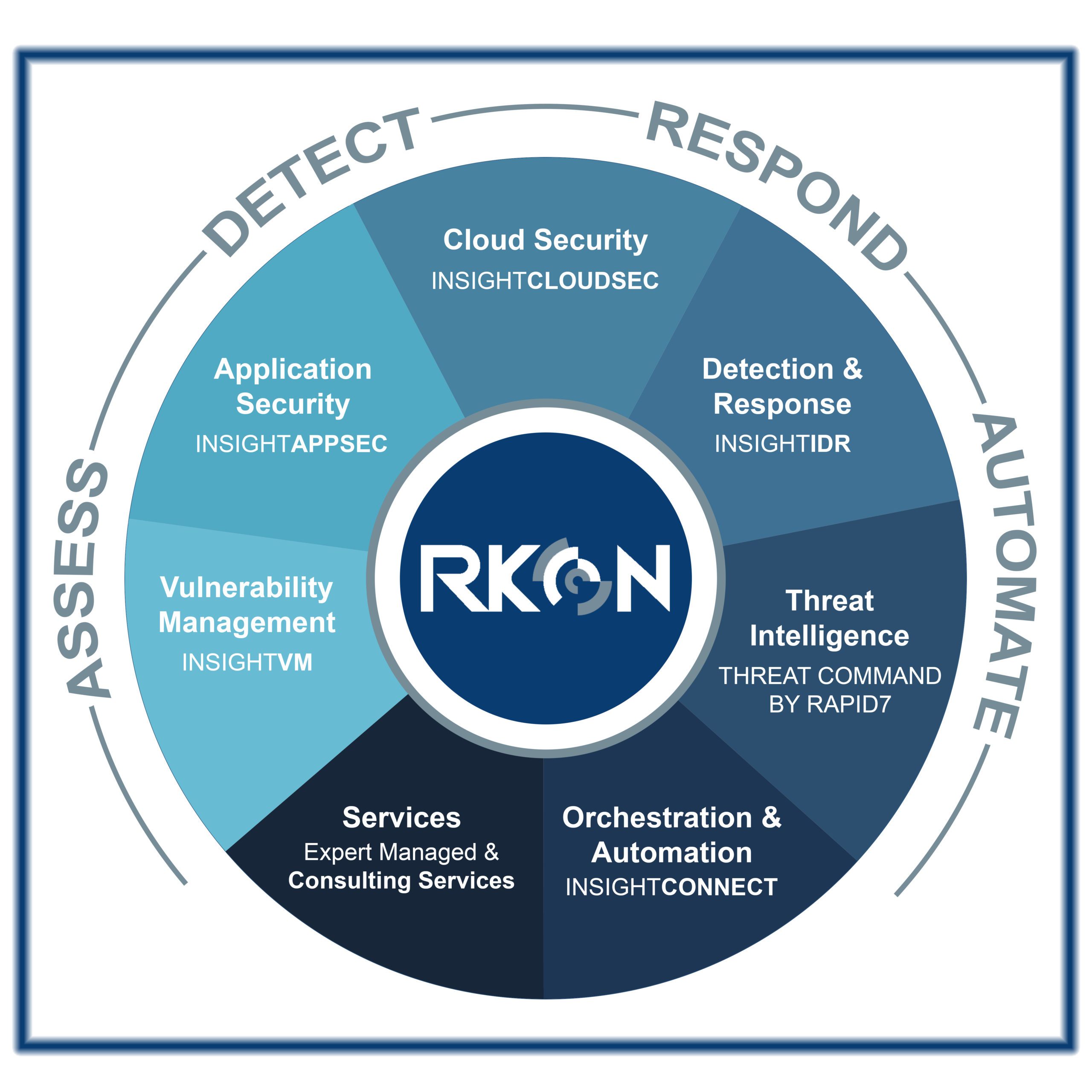
RKON delivers security breach recovery services using our ISO20701 certified security and vSOC platform. This platform is responsible for 24/7 security monitoring and management of hundreds of private equity and mid-market organizations. Our security breach recovery services provide comprehensive security coverage including cloud security, detection response, and vulnerability management for all major cloud & saas providers; in addition to user legacy and data center assets.
- Configuration Posture Management
- Compliance and Governance
- Identify Access Protection
- Workload Protection
- Code and Container Scanning
- Centralized Log Management
- Endpoint Detection and Visibility
- User & Attacker Behavior Analytics
- Visual Investigation Timeline
- File Integrity Monitoring
- Lightweight Endpoint Agent
- Real Risk Prioritization
- Live Dashboards
- Container Security
- Threat Intelligence Integration
Security Breach Recovery Service Overview
Security Breach Recovery Standard Timeline
Our engagement process covers four stages of security remediation and begins with Breach Recovery Initiation. When a security breach occurs our dedicated team of white-hat hackers will identify its point of origin to assess and contain any damage. We provide vCISO oversight to establish communications with key stakeholders including clients, vendors, and investors.
Next, our team focuses on detection and analysis. RKON’s difference is our ability to bring deep experience and certifications to the technologies that have been effected. This allows us to take a hands on approach to securing and remediating your IT environment. We deploy a set of AI based tools on all IT & business assets including desktops, servers & cloud instances. These tools give us immediate visibility to help isolate infected elements and sources.
Within 48 hours, our security team will have identified the root source of the breach and will establish operational oversight and change management protocols during the containment & isolation phase of our security breach recovery.
On average, baseline recovery will take 2-5 days. RKON engages the operations team to bring technology specific resources to help with hands on activities including:
- Security patching
- Rebuilding systems
- Misconfiguration remediation
- Backup & restore
RKON stages recover by prioritizing mission critical assets first. We bring you back online in the shortest time possible by isolating elements of your environment that may take longer to remediate. Our success rate is 100%, but unless some precautions are taken before a breach, we can’t guarantee the complete recovery of all data. To learn more about preventive measure your organization can take to protect against security threats, check out our Managed Detections Response (MDR) services.
Assess Your Cloud Environment Today
Are you a private equity or mid-market organization that has been breached and needs help with recovery contact us at (312)-654-0300, and leave a message for our support desk. We will get back to you in 15 minutes.
Contact Us Today
If you are looking for more information about our IT Transformation & Security services please don’t hesitate to reach out. Our team of IT experts is ready to help.
Call Us
Get Started Today
RKON’s Security Leadership Team

Chris Hueneke,
Chief Information Security Officer

Joe Knape,
Security Advisory Manager




