Security Assessment:
Is Your Cloud Secure from Vulnerabilities?
Cybersecurity threats are on the rise and causing significant business disruptions including loss of operations, revenue, equipment damages, employee & customer data, and large PR expenses. With these threats on the rise and many organizations already impacted, a cybersecurity risk assessment will evaluate controls, scan for vulnerabilities, and simulate an attacker to expose weakness in security posture. This assessment can help save your organization a lot of time, money and resources by identifying, remediating & protecting against the on-going threat of hackers & cybersecurity criminals.
RKON’s On-PAR Cybersecurity Assessment
Our cybersecurity assessment helps organizations review, remediate and secure their IT infrastructures against potential or on-going cybersecurity threats and vulnerabilities. We leverage our On-PAR security assessment framework to analyze your organizations current-state administrative, technical, and physical security controls giving allowing us a complete picture of your IT environment. In leveraging our on-PAR Assurance we ensure that our clients have appropriate and cost-efficient security measures implemented while meeting compliance expectations with regulatory and industry requirements. Our security assessment & validation process includes:
- NIST Cybersecurity Framework
- Security Controls Reviews
- Automated Vulnerability Scanning
- In-depth Penetration Testing
- Infrastructure, Applications, Cloud
Our security team reviews internal and external threats, vulnerabilities, and security controls leveraging ISO 27001 and NIST Cybersecurity Framework best practices, helping to determine risks to the organization. These reviews cover administrative controls, technical controls (i.e. threat management solutions), physical controls, regulatory and industry compliance standards, as well as current “as-is” state security architecture reviews.
Cybersecurity Assessment Deliverables
As an end-to-end security provider we want to ensure our clients have a proper path forward once assessment is complete. Once we have reviewed your current state security and security architecture you can expect several deliverables from our security team including:
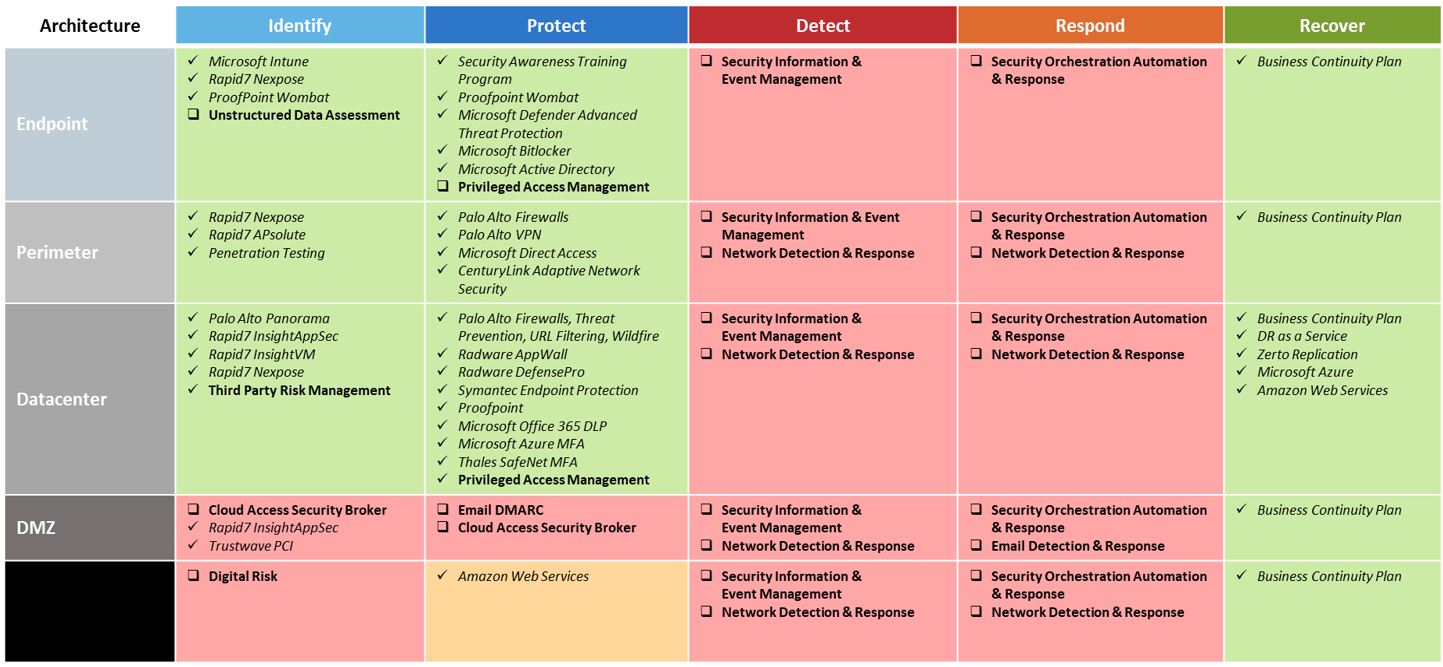
- A recommended future ‘to-be’ state security and disaster recovery architecture that aligns with the National Institute of Standards and Technology (NIST) Cybersecurity Framework (Identify, Protect, Detect, Respond, and Recover) best practices across Endpoint, Perimeter, Datacenter, DMZ, and Cloud.
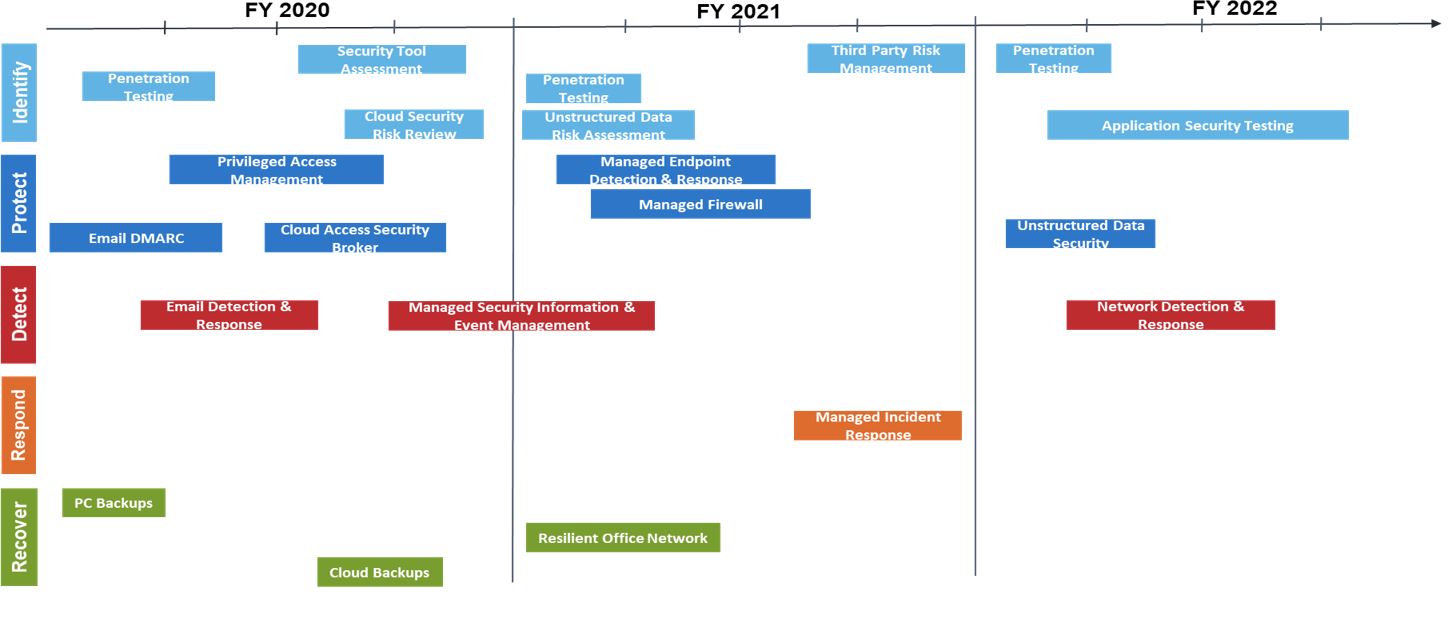
- A three-year IT security & disaster recovery roadmap, project list, and budgeted costs to address recommended solutions and services.
- A IT Risk Register highlighting risks and remediation identified throughout the review
- Complete review of results from deliverables to your key stakeholders
With extensive testing and review process experience, encompassing an organization’s entire security architecture, we are ready to help secure your organization. Contact the RKON security team today for more information on getting you started with a security assessment.
Contact Us Today
If you are looking for more information about our IT Transformation & Security services please don’t hesitate to reach out. Our team of IT experts is ready to help.
Call Us
Get Started Today
RKON’s Security Leadership Team

Chris Hueneke,
Chief Information Security Officer

Joe Knape,
Security Advisory Manager