Have you ever received an email with lucrative, eye-catching offers that are too good to be true? Or one from a trusted entity saying they need you to wire money, download an attachment, or click on a link? Unfortunately, you’re not the first person targeted by these seemingly legitimate emails or text messages. In fact, you’re one of many lured into providing sensitive data, including personal information, credit card details, social security numbers, and passwords, to cybercriminals.
There are thousands of phishing campaigns like these launched every day, and they often succeed in accessing victims’ accounts. With increasing sophistication, companies and individuals must take preventive measures to identify and eliminate these widespread and pernicious attacks.
To help you better detect malicious activity, let’s break down some of the most common features of a phishing email:
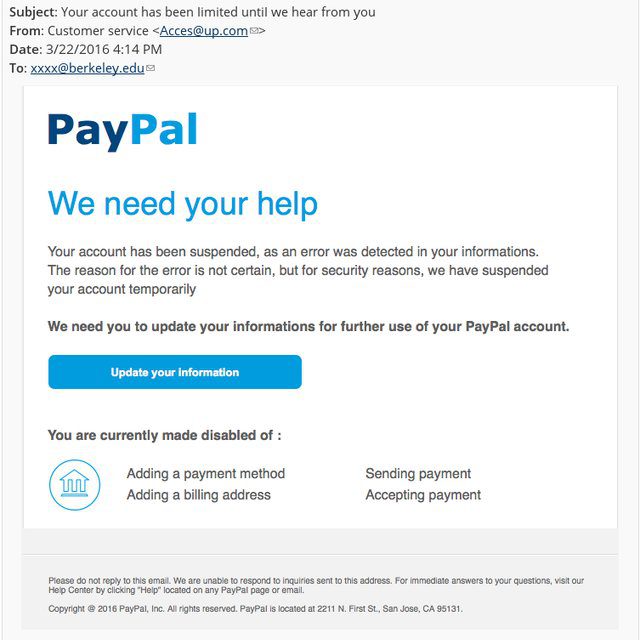
Let’s look at an example:
Looking at the email below there are a few things to notice:
- The email address of the sender is NOT from PayPal ([email protected]).
- Poor grammar in the message.
- The “update your information” link, sends you to a malicious site that’s not associated with PayPal.
Without looking too closely, this email seems valid, and scammers who send emails like this one often get the information of victims, which can have real consequences for individuals and the companies they’re targeting.
How to spot possible phishing attempt:
First, it is important to know the common features of a phishing email so that when you receive an email from a trusted source, you can quickly identify whether or not it’s safe. To quickly and reliably identify scams, here are some common indicators to be aware of:
- Be careful who you trust:
- Scammers often use familiar company names or people as bait, quickly luring you into making a mistake. Pay attention to the sender’s email address. Usually with phishing scams, the email address does not align with the appropriate company or individual, giving you an obvious indicator that this is not a reliable source.
- Act fast!
- One of the most frequent tactics used by cybercriminals is to instill an extreme sense of urgency: act fast or the super deals will be gone! They even go as far as to say your account will be suspended if you do not respond within a few minutes. Trusted companies rarely ask patrons to provide personal details over the internet, so it’s best to ignore these types of emails.
- Hyperlinks.
- Unsafe text messages or emails often include a link, in which the content of the email is urgently directing you to click on it. Look carefully because most of these links send you to a malicious site designed to resemble a trusted site.
- Download Attachments.
- In 2018, the FBI’s Crime Complaint Center (IC3) reported nearly 1,500 ransomware attacks against individuals, businesses, and organizations, totaling nearly $3.6 million in losses. Ransomware developers use pop-ups or email attachments to access your personal information, so beware of downloads unless you’re expecting files and know they’re safe.
Don’t get hooked: Phishing prevention tips
Instead of falling victim to future phishing attacks, you can implement these proactive measures to protect you and your organization from being hooked:
- Be skeptical. Take the time to double-check all emails. Make sure you know who the email is from, get confirmation before downloading any attachments, ignore all reward scenarios involving some kind of prize, and hover over links to make sure they direct you to valid, safe sites.
- Use updated security software. While many spam filters can prevent phishing emails from entering your inbox, cybercriminals are learning how to outsmart these filters. Add an extra layer of protection by setting up automatic software updates so you’re always protected against the latest threats.
- Ignore emails with commands or requests. If you receive an email, even from trusted entities, asking you to do something, immediately look for scam tip-offs. Be especially wary if you don’t have an account with the company, the message contains misspellings or bad grammar, or the content asks you to click on a link or download an attachment.
- Consider multi-factor authentication. If you’ve received an email you’re unsure of, set up a second step to verify who you are on accounts that support it.
- Change passwords frequently. Another way to add extra security is to change your passwords on a regular basis. Additionally, avoid using the same password for multiple accounts. If your passwords do become compromised, change them immediately and don’t use them for any other accounts.
- Double-check Links and attachments. If there is a link in an email, hover over the URL. Usually, if the link is malicious, it will have typos, wrong domain names, or an invalid Secure Socket Layer (SSL) certificate. Additionally, if you receive a download from a reliable source, verify with the sender before installing. If unsure, log on to the official website or contact the actual business instead of clicking on the link in an unsolicited email.
- Focus on awareness and training. Each year, phishing scams are growing more and more sophisticated as ransomware techniques and malware evolve. Contingency and remediation planning is crucial to protect businesses and ensure the integrity of sensitive data. Since employees are often targeted, they need to be made aware of these threats, how they’re delivered, and what security principles and techniques can prevent future security events. If trained on robust prevention controls, employees can protect themselves and their companies from exploitation.
Note that phishing criminals are quickly becoming emboldened with new strategies to hook lucrative enterprises and employees into crippling their organization. Investing in backups and other cyber defenses, like employee training, is critical to prevent attackers before it’s too late.
As a leading IT Transformation & Cybersecurity advisory practice, our team has deep consulting and execution expertise in digital transformation, platform creation, and operations management. Our industry experience is rooted in our passion, integrity, and commitment to finding the best-possible IT solutions for our clients.