COVID-19 has quickly dismantled businesses in terms of operational efficiency and security. Supporting your help desk as companies adjust to the full-blown adoption of telecommuting is now essential. We’ve put together a list of questions and best practices to help you execute with ease.
1. Are Organizations Ready for Remote Work?
The vast majority of organizations are unprepared to suddenly move their entire workforce to a remote model, placing tremendous strain on IT teams and help desk providers. We’ve seen requests skyrocket as businesses scramble to create an efficient, secure, and effective workforce. Empowering your help desk to manage these unprecedented scenarios will make or break your telecommuting strategy.
In order to avoid disruption in the long-term, IT leaders should focus their efforts on addressing immediate needs for remote employees, like installing Virtual Private Networks (VPNs), enforcing end user training, promoting security awareness, remediating technology infrastructure as needed, and reassessing business continuity plans. In doing so, leadership can facilitate adept policies, regulations, and best practices that identify and sustain secure solutions that protect the viability of the business.
2. How can IT Departments Help Leadership Manage their Teams?
First and foremost, it is crucial to ensure that your infrastructure can accommodate a remote working environment. C-suite leaders and IT departments must conduct risk analysis to evaluate the equipment, technologies, and processes in place and prioritize those that are most suitable to block potential security risks during remote collaboration.
Along these lines, it’s also critical to help employees on the home front, enabling their capacity to not only use their devices remotely, but to do so without risk of compromising assets and data. If you update your IT policies to make them applicable to remote working environments, then you can enhance training and awareness for employees, boosting their ability to detect and prevent potential scams or malicious activity.
Essential questions that all IT departments should be asking right now include:
- What is our current email phishing prevention toolkit?
- What is our current backup and restore policy?
- Is the disaster recovery and incident response plan well documented?
- Are users receiving security awareness training?
- Are vendors being assessed for risk?
3. How do we Keep our Remote Workers Secure?
One of the most important steps to securing your remote workers is implementing Virtual Private Network (VPN) technologies that allow personal devices to smoothly transition onto your corporate network. This protects employees working on their home Wi-Fi by giving them an encrypted connection, which prevents unauthorized traffic and safeguards company data.
Additionally, some key protections during this time include facilitating risk analysis, layering controls on remote access services, such as endpoint security controls and two factor authentication, and providing consistent formats for reporting compliance and risk.
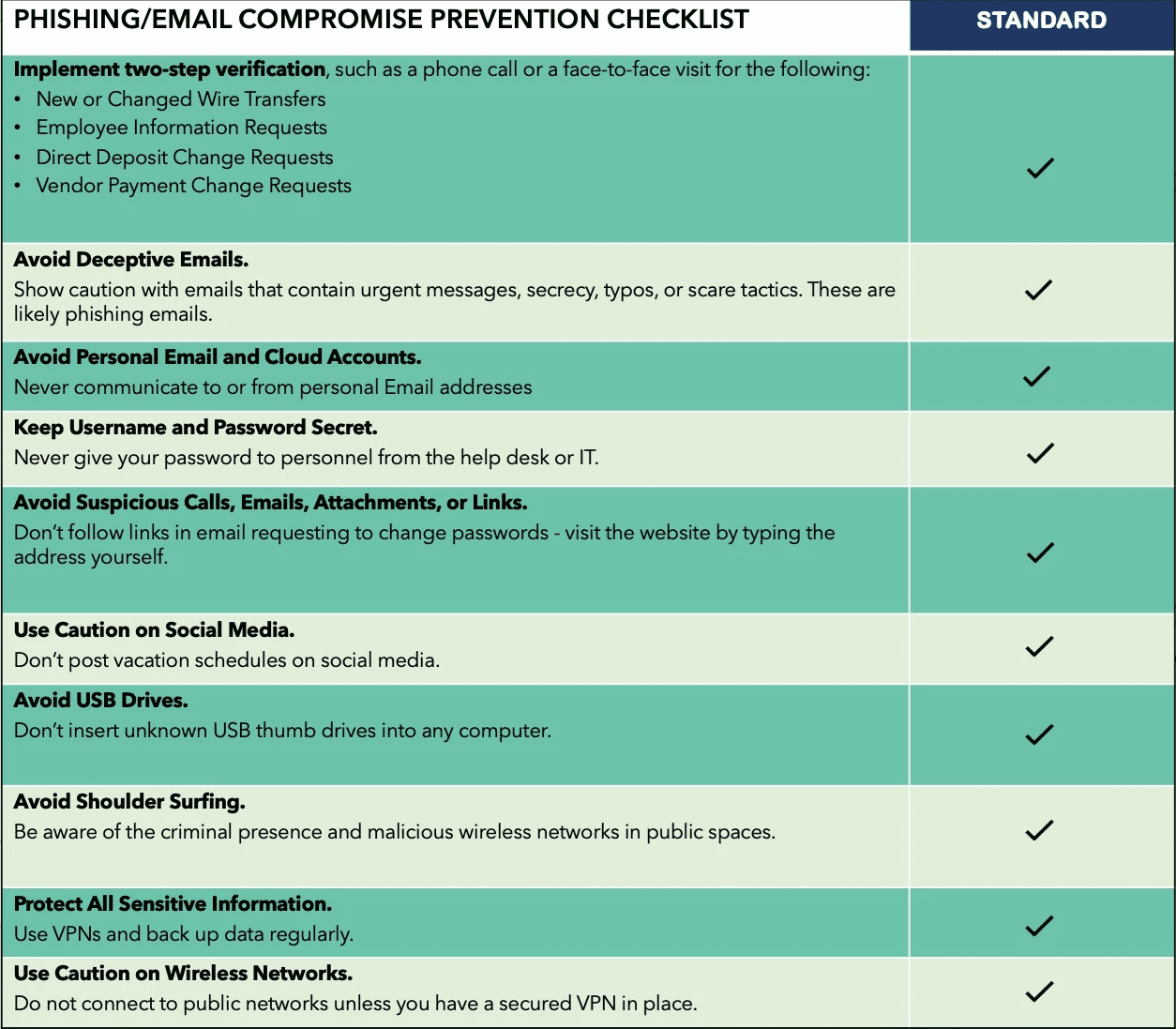
Hackers are using the sudden shift to remote work to their advantage, and employees must be trained on how to spot malicious activity. RKON has put together a phishing/business email compromise prevention checklist to help with your security awareness and training:
4. What are some Best Practices to Support your Help Desks?
Remote access means increased exposure, and our help desk providers are under a lot of pressure to help businesses prevent security mistakes down the line. Because businesses are unprepared for the consequences of virtual work en masse, they are attempting to piecemeal together untested solutions, causing real security gaps.
The best way to support your help desk is to make sure they are equipped with the right tools to reduce the burden on leadership. Assess your troubleshooting processes and technologies to make sure they’re fit to overcome remote challenges. This could mean conducting holistic crisis scenario analyses to improve your recovery strategy and optimize business continuity or implementing remote-assistance software.
Use these tips to make sure your IT department is in the position to succeed:
- IT Security Policies are documented, communicated, and accepted by users;
- Security Awareness Training is provided to end users;
- Security Architecture implemented to Identify vulnerabilities, Protect against threats, Detect attacks, Respond in a timely manner, and Recover to keep the business operational and resilient;
- Security Operations Center is monitoring threats and vulnerabilities, reporting on performance of security controls and handling incidents; and
- Disaster Recovery Plan is documented, reviewed, accepted, and tested regularly.
5. What are some Best Practices to Support your Business Long-Term?
Businesses want to capture effective continuity plans that seamlessly support the prevention of threats and recovery of operations. The goal is to enable ongoing operations, even in the face of drastic and unprecedented change, like the shift to remote work.
A comprehensive preparedness plan will formulate practical recovery strategies that foster a resilient and stable environment. In order to achieve this, RKON has highlighted some key components of business continuity that will help you test, measure, and update systems as needed:
- Virtual Chief Information Security services provided by strategic partners;
- Risk and Security Self-Assessment performed across the business and portfolio companies;
- Security Architecture Review analyzing control gaps and remediation;
- Monitor Security and Risk Posture continually across the business; and
- Business Continuity Plan includes Crisis Management, IT Disaster Recovery, Security Incident Response policies, processes, and subject matter experts (internal team and external partners)
Be Proactive
When all is said and done, the most important key to protecting and managing your remote business is to stay proactive. Establish internal department rules, follow up financial requests with a phone call, keep up with security awareness training, and continuously monitor and assess security and risk posture across the business. This will not only benefit your help desk, giving them the tools and support they need to respond efficiently and effectively, but it will also keep your remote employees aware and prepared to avoid suspicious cyber activity.
As a leading IT security advisory practice, our team has deep consulting and execution expertise in digital transformation, platform creation, and operations management. Our industry experience is rooted in our passion, integrity, and commitment to finding the best-possible IT solutions for our clients.